The Canadian government is currently struggling with a data breach that took place sometime in September. It affects both current and former Canadian government employees, and members of the RCMP and Canadian Armed Forces.
According to what we have learned so far, personal and financial information dating back to 1999 was compromised as part of the breach.
Let’s dive into the details and see what caused it and what the Canadian government is doing to protect the victims.
Source of the Data Breach
Two companies, Brookfield Global Relocation Services (BGRS) and SIRVA Worldwide Relocation & Moving seem to be the source of the breach. Both companies provide relocation services and support to federal government employees.
The Treasury Board announced the breach on October 19, but the timeline indicates it occurred much earlier. SIRVA's data was stolen by the ransomware group LockBit in early October and leaked on November 19 after failed negotiations. BGRS's website has been offline since September 29, suggesting a breach around the same time.
It is unclear how data going back over 20 years was accessed. The amount compromised is also unknown, with the Treasury Board unable to identify impacted individuals due to the vast quantity involved. They are taking steps to mitigate potential harms but have provided few details.
Details on the SIRVA Breach
For SIRVA, LockBit claimed to have 1.5TB of documents and backups of customer files. After failed attempts to negotiate the initial $15 million ransom down, they leaked SIRVA's data. The chat log shows SIRVA's negotiator tried to gather information and repeatedly delayed, angering LockBit.
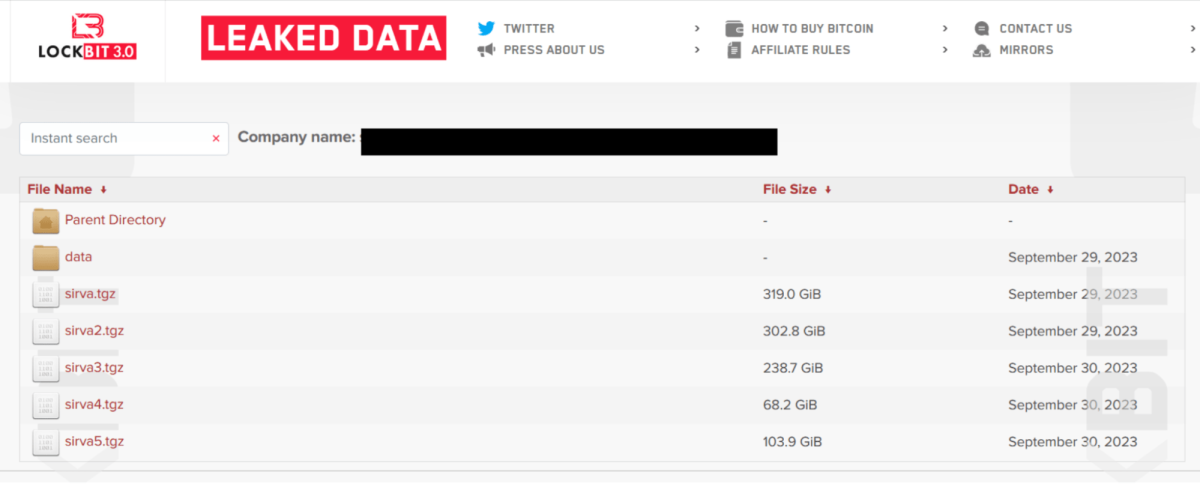
More than 1 TB worth of files from SIRVA were leaked. (Source: databreaches.net)
The final offer of $1 million was rejected. LockBit refused any discount over 50% of the original demand. With no agreement reached, the data dump occurred.
Uncertainty Around BGRS Breach
As of yet, we don’t know how much data LockBit stole from BGRS. If their claims are true, then there’s a possibility that we’ll see more data leaks in the coming months, especially if BGRS refuses to pay ransom.
The group may try to profit by selling the data. It's unknown if negotiations are ongoing or if BGRS's data has already been dumped alongside SIRVA's.
Implications for Impacted Individuals
If you have been impacted by the breach, then you may be at risk of identity theft, fraud, extortion, and other malicious activities. The Canadian government, in response to concerns raised by government employees, has recommended that you should constantly monitor your financial accounts and report any activity that seems suspicious.
This incident represents a worst-case scenario for a data breach. The lack of details and timeline leaves many unanswered questions. How was so much data from 20+ years accessed? Why did robust security measures fail? And will lessons be learned to prevent similar breaches in the future? The government owes better protection and transparency to those impacted.
As more details emerge, the complexity and severity of this breach will come into focus. For now, those affected face an anxious wait as the government scrambles to manage this crisis. The potential damage to national security and personal finances remains unknown. But this historic failure to secure sensitive data will likely have far-reaching implications.


