Omaha, Nebraska-based DRM Corporation, a family-owned franchise group operating 73 Arby's restaurants across four states, has become the latest victim of a cyberattack perpetrated by the notorious Cactus ransomware group.
With hundreds of employees and countless customers, the company handles a huge amount of sensitive data that may now be at risk. Here’s what we know about the attack so far:
Attack Scope and Impact
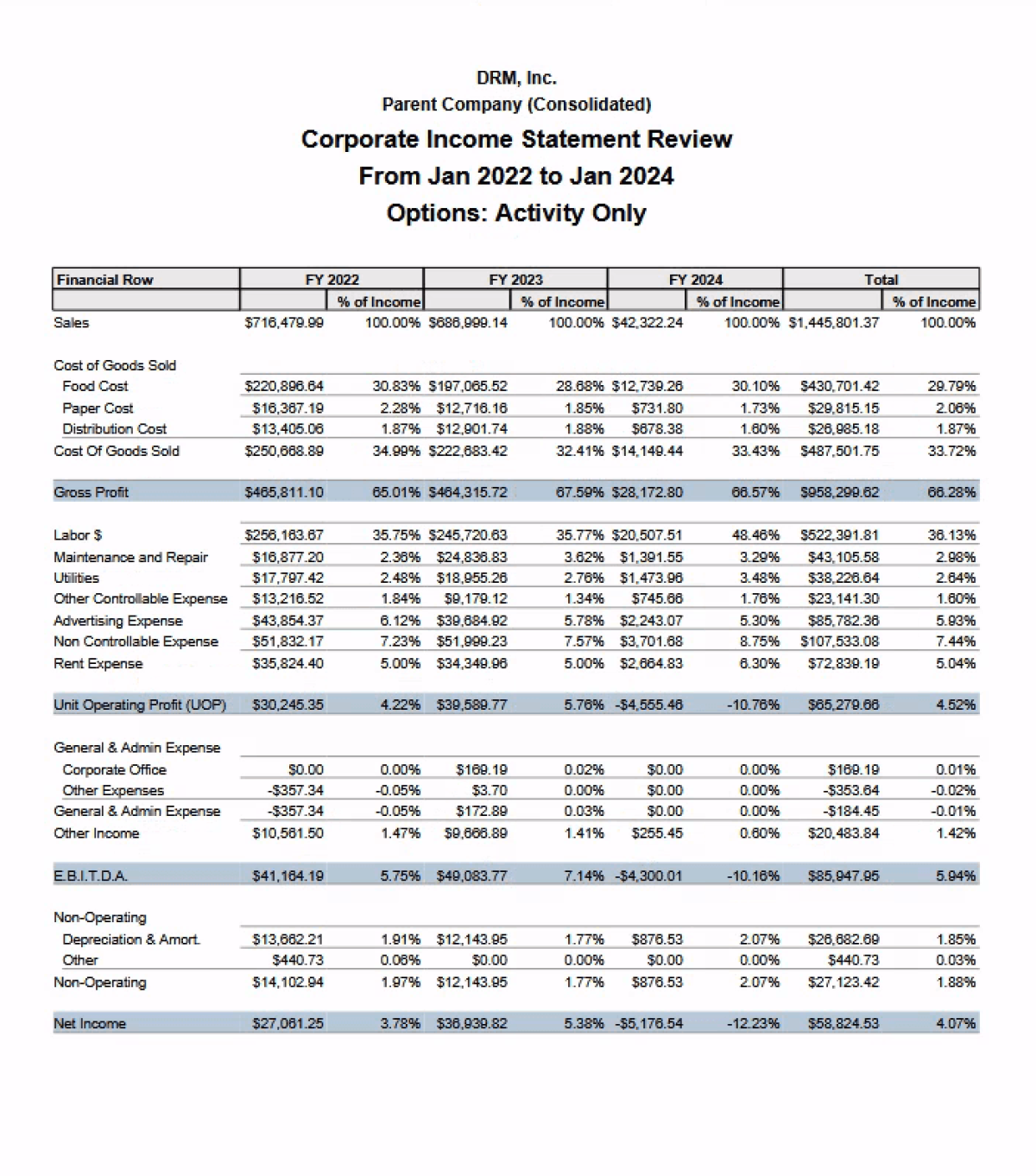
From our reports, we suspect that DRM's computer systems were infiltrated with Cactus ransomware, a malware program that encrypts data and renders it inaccessible. Not only could this cripple DRM's operations, hindering functions like order processing, inventory management, and customer communication, it also meant that the data was stolen before encryption.
The extent of data encrypted and stolen during the attack remains unclear apart from the statements made by the Cactus group itself, who claims to have exfiltrated a substantial 175 GB of data from DRM's systems.
According to Cactus, this information breach encompasses accounting and payroll documents, personally Identifying information, HR documents, contracts, corporate correspondence, employees and executive managers personal folders, and more.
With over 400 employees at risk, there is now a lot of uncertainty about job security at DRM, particularly if the attack significantly impacts operations. Concerns about potential exposure of personal data are at the forefront, with pictures of employee driver’s licenses being uploaded as proof of the hack on Cactus’ blog.
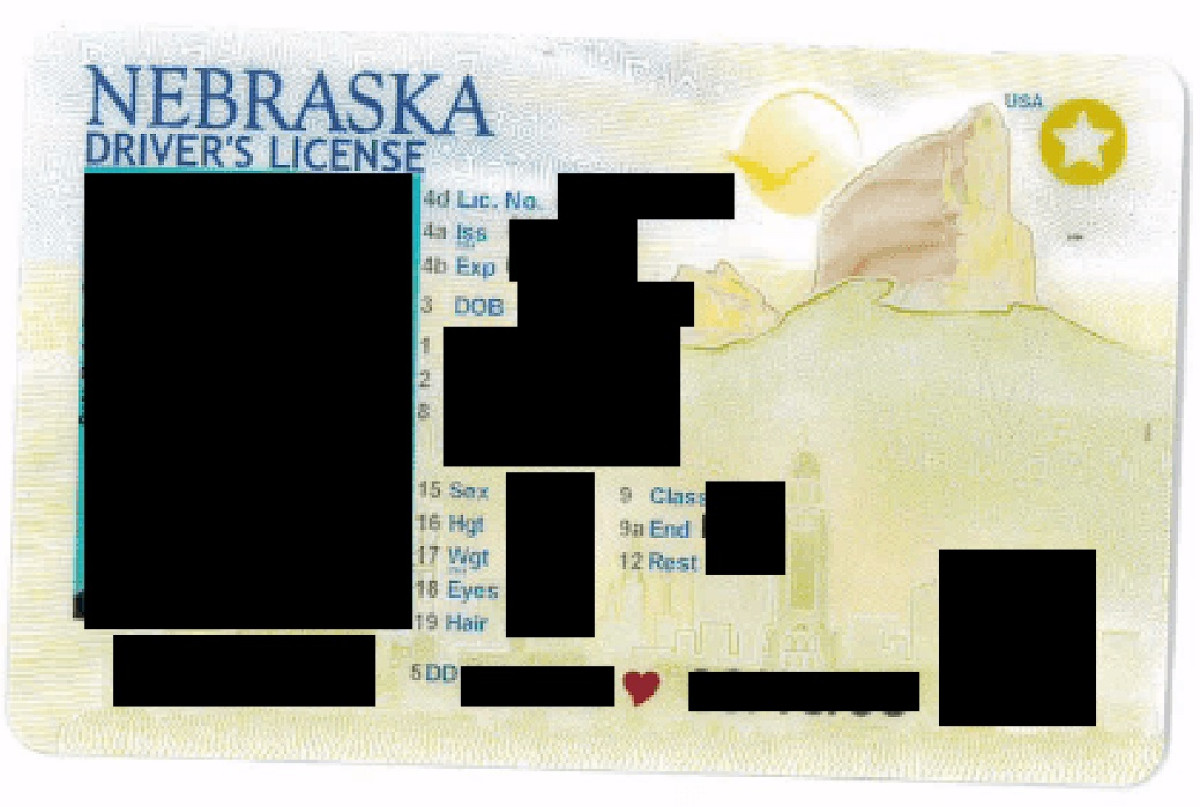
The risk certainly extends to customers as well, who are worried about the security of their financial information used at DRM locations (any one of 73 different Arby’s across four states). If customer data like names, addresses, or credit card details were compromised, they could be at risk of identity theft or fraudulent charges.
Though there wasn’t any such data uploaded as proof on the ransomware group’s blog, we have reason to be concerned nevertheless. The attack also certainly erodes customer trust in DRM's ability to safeguard sensitive information.
Who is Cactus?
The Cactus ransomware group was first seen as a major threat in March 2023, so they’re relatively new to the scene. That hardly means they’re amateurs though - their origins and identities remain shrouded in secrecy, but their actions paint a concerning yet clear picture. Cactus operates with a ruthless efficiency.
Their primary mode of attack is exploiting known vulnerabilities in commonly used software, particularly VPN appliances and Qlik Sense data analytics platforms, to gain initial footholds within target networks. Once inside, they reportedly use a combination of batch scripts and self-encrypting ransomware to maximize the severity of their attack.
This self-encryption tactic makes detection almost impossible, which is how they’re able to encrypt and steal a large amount of data before anyone even notices something is wrong.
The group also uses a "double extortion" approach, where they not only encrypt their victims’ data but also steal sensitive information before encryption. This stolen data, as we’ve seen in this report, is a powerful bargaining chip that they use to pressure victims into paying a hefty ransom for both data decryption and the prevention of the stolen information's release.
Cactus’ ruthlessness was on full display in another one of their recent attacks, which was arguably their biggest to date, on Schneider Electric in January 2024. In this attack, they stole 1.5 terabytes of data and threatened to expose it if their demands weren't met. We don’t know what the full extent of Cactus's operations and their leadership is, but their rapid rise to the top have certainly got them on every cybersecurity individual’s radar.
Cactus’ Motivations and Demands
The primary motive behind ransomware attacks such as this is typically financial gain. While the details were not disclosed in this regard, the Cactus group likely demanded a hefty ransom payment from DRM in exchange for decrypting the compromised data and refraining from further publishing the entirety of the stolen information.
Since these negotiations primarily happen in private conversations between the parties, we do not have exact details on them as of yet.
Current Situation
The current state of DRM's operations and the status of their data are undetermined, but given the images posted to Cactus’ blog, it’s safe to assume that a considerable amount of both have been compromised.
At this time, the importance for DRM to prioritize data recovery, system restoration, and a thorough investigation to identify vulnerabilities exploited in the attack is at its pinnacle. Once they understand how this happened, any future attacks can be prevented.
Plus, if customer data was compromised alongside the employees’ information, DRM has a responsibility to notify affected people and take measures to prevent any harm from coming to them.
Implications for Everyone Else
The DRM Arby's attack is the latest reminder of the concerning fact that cyber threats faced by businesses of all sizes are becoming more frequent at an ever-increasing rate.
The restaurant industry, which often handles sensitive customer information like credit card details, is a prime target for cybercriminals. Although a certain amount of damage has been done, we believe DRM should still adopt these security measures to keep their systems and data safer in the future:
- Employee Training: Include cybersecurity best practices about topics like phishing email identification and secure password management.
- Security Software: Firewalls, intrusion detection systems, and endpoint protection software are the first line of defense against malware intrusion - they need to be on point.
- Patch Management: Make sure your software always has the latest security patches which can address known vulnerabilities that attackers might exploit.
- Data Encryption: Sensitive data (such as employees driver’s licenses) should be encrypted, making it difficult for it to be compromised even if it is stolen.
Unresolved Questions About the Attack
How did the Cactus group gain access to DRM's systems? Did DRM pay the ransom demands yet? Our attempts to contact DRM also went unsuccessfully - is DRM taking any steps to address the security breach and protect customer information? As of now, what we do know is that law enforcement and cybersecurity teams are investigating the attack.
Moving forward, it’s important for DRM to be transparent about the incident's details and their response plan in light of it.
For our readers, let this be a reminder that in today’s digital world, cybersecurity is one of the most important aspects of conducting business safely and should be addressed accordingly.


