For the past two weeks, a relentless cyber assault by the hacker group NoName has been targeting critical Ukrainian infrastructure. The group, whose motives are believed to be aligned with Russia's ongoing military operations, has launched a sustained Distributed Denial-of-Service (DDoS) campaign, aiming to cripple essential online services.
With the conflict between Russia and Ukraine still raging, this development puts the latter in a fair bit of danger in the cybersecurity realm. Here’s what we know so far.
Is NoName a Digital Pseudonym for Russia?
The true identity of the NoName hacker group is unknown as of now and is likely to remain that way. However, having analyzed their activities and attacks, we can craft a threat profile with a reasonable degree of accuracy.
NoName almost certainly operates with the tacit approval, or even direct support, of the Russian government. Their attacks align with Russia's overall strategy in the Ukraine conflict - disrupting essential services and spreading chaos within the country. Some analysts suspect NoName could be a state-sponsored group, a well-funded "patriotic hacker" collective, or even a group of freelancers contracted by the Russian government.
Despite their lack of public identification, NoName is second to none in their level of technical sophistication. Their sustained DDoS attacks most certainly require a large amount of computing power and knowledge of complex network exploitation techniques. This further suggests that NoName could be a well-coordinated group with access to substantial resources.
Opinions differ on NoName's structure. Some state they're a lone-wolf actor, possibly a single skilled hacker launching the attacks, but we believe the consistency and frequency of their attacks point towards a more organized group with a clear division of labor. All that is certain for now is that they are a dangerous threat to any nations and/or coalitions that are on opposing sides to Russia in the Ukrainian conflict.
The Targets and Impact
NoName’s DDoS campaign in Ukraine has targeted many parts of the country’s digital infrastructure. Disruptions and ripple effects have been felt across various sectors as a result:
Government Services
Early targets included the websites of the Ukrainian Ministry of Defense and the National Bank of Ukraine. These disruptions hinder Ukrainians' ability to access essential services online, such as filing taxes, registering for social programs, or even renewing passports.
For businesses, delays in government approvals or permit processing have led to lost revenue and economic hardship. The official portal of the Verkhovna Rada, Cabinet of Ministers, and State Tax Service of Ukraine are among the affected areas.
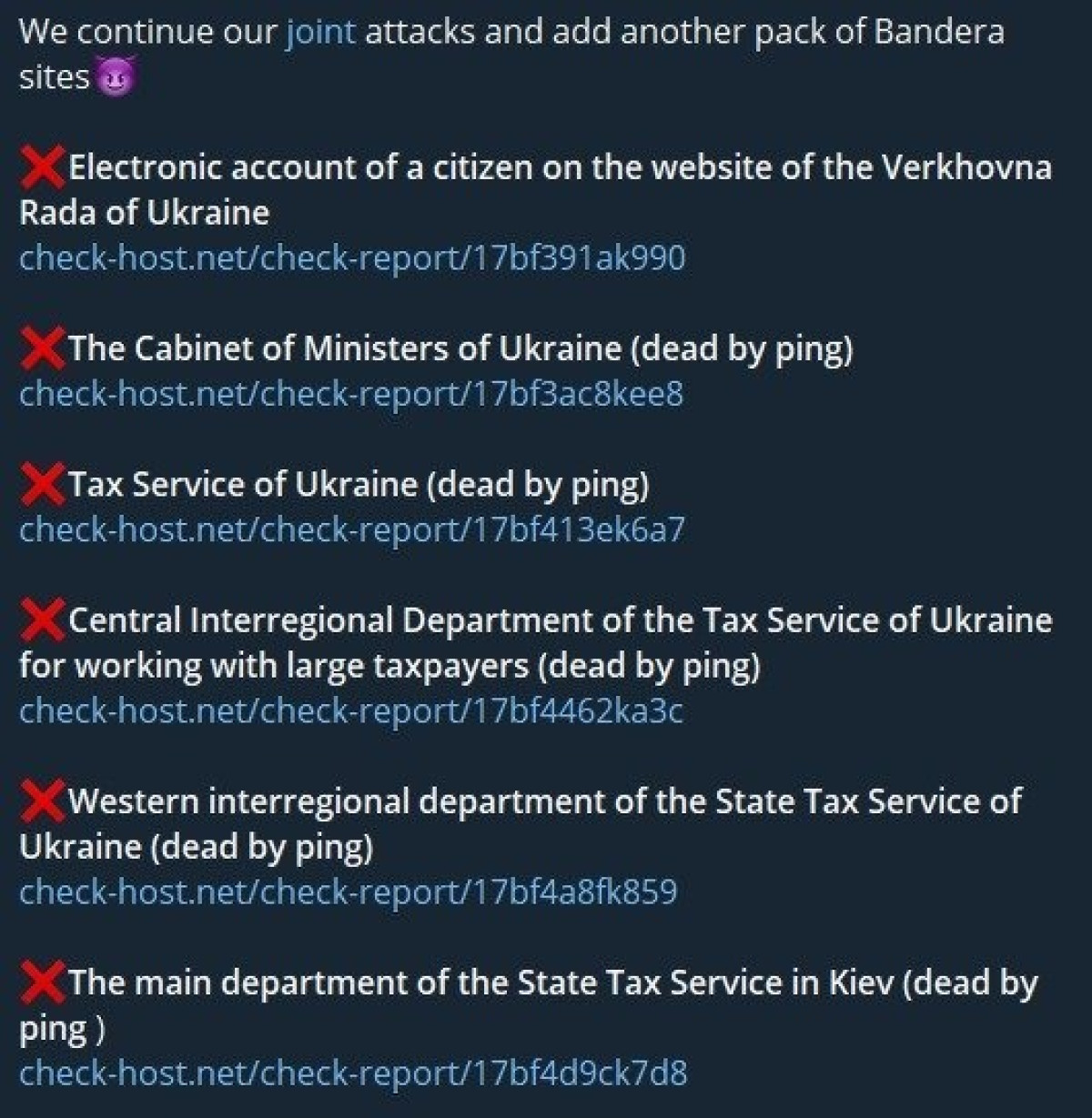
A tweet by NoName listing the sites they’ve attacked.
Financial Institutions
DDoS attacks on Ukrainian banks have almost crippled online banking services, with people being unable to access their accounts, make payments, or transfer funds. This has caused panic and disrupted essential financial transactions for citizens and businesses alike.
Salaries are being delayed and people are unable to pay essential bills due to inaccessible online banking systems. UnexBank and KredoBank are among the most severely affected financial institutes.
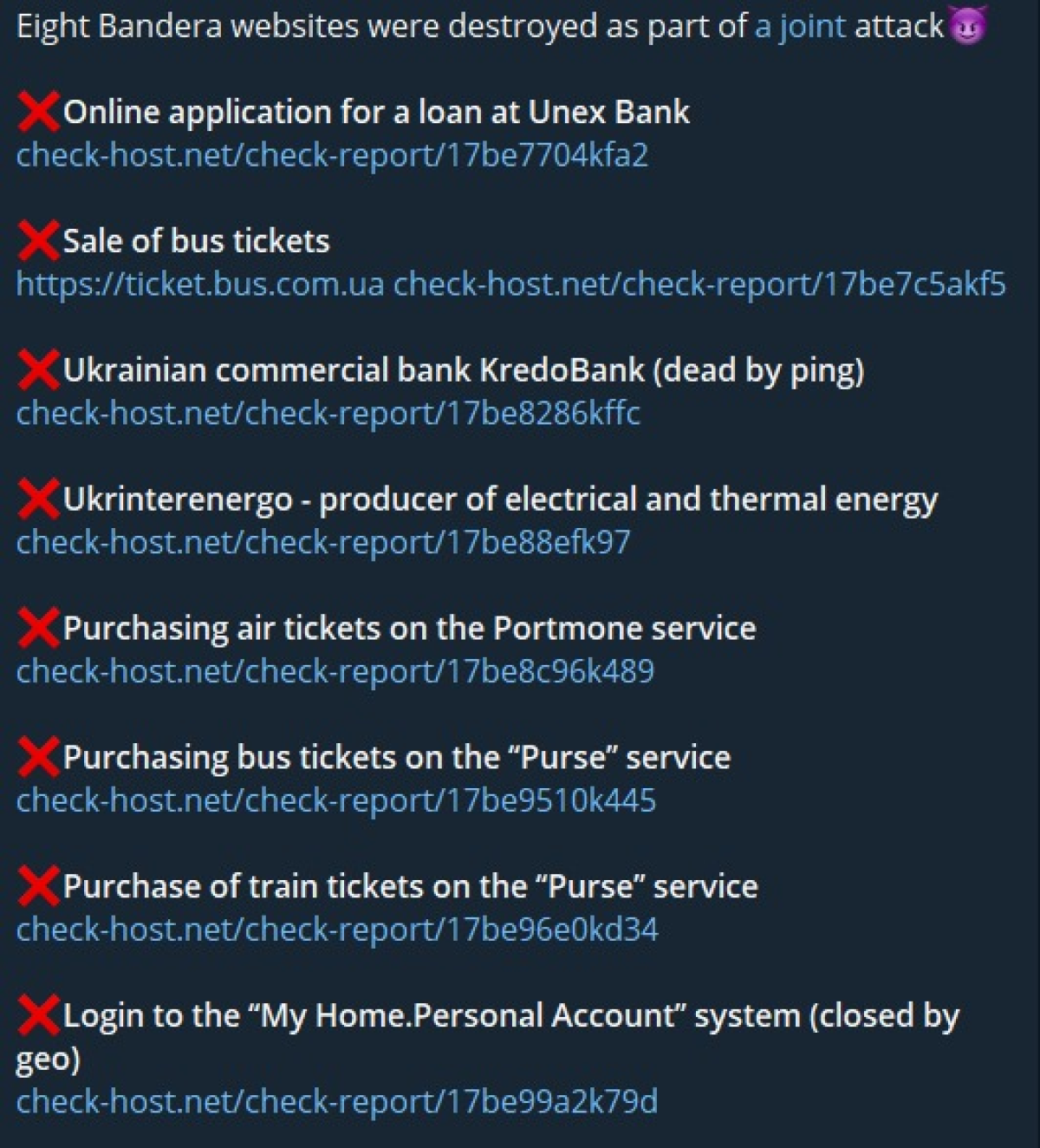
Another tweet by NoName listing more sites that have been targeted.
Critical Infrastructure
Perhaps the most concerning threat of NoName's attacks is their targeting of power grid control systems and transportation networks. While successful infiltration attempts haven't been documented, the group has shown successful DDoS attacks on a power grid control system.
This could trigger blackouts, disrupting hospitals, communication networks, and even water treatment facilities in the country. Similarly, the targeting of transportation networks (bus, train, and plane ticketing portals) has created disruption in railway schedules, air traffic control systems, and even disabled crucial communication channels for emergency responders.
Independent Media
NoName has even attacked independent media outlets, with the aim to disable the flow of information and sow discord within Ukraine. By taking down news websites and social media platforms, the free press will be significantly challenged, making it difficult for Ukrainians to access objective reporting on the current situation.
With the fog of war already making things bad, this lack of transparency will only make matters worse for public morale and make the spread of misinformation a lot easier.
Understandable, the impact of these attacks goes beyond immediate inconveniences. They have and will continue to cause economic damage, hinder communication during emergencies, and erode public trust in essential institutions. The Ukrainian government, businesses, and citizens are all feeling the ripple effects of this ongoing cyberwarfare.
Ukrainian Response and International Support
Ukrainian cybersecurity teams are reportedly working around the clock to identify and filter out malicious traffic targeting critical infrastructure and government websites. Traffic filtering, IP blacklisting, and distributed denial-of-service (DDoS) mitigation tools are among the tools currently being employed to absorb the attack load and keep essential services online.
International organizations like NATO's Cooperative Cyber Defense Centre of Excellence (CCDCOE) have been key in coordinating international support for Ukraine. International support has played a critical role in the conflict from the very beginning.
In this specific attack, international partners are sharing cyber threat intelligence with Ukraine, including information on NoName's tactics, techniques, and potential future targets. This information is invaluable in helping Ukraine anticipate potential attacks and proactively implement countermeasures.
Projecting the Road Ahead
What’s going to come next in the NoName campaign remains unclear. The group may escalate its attacks, targeting critical infrastructure with more sophisticated tactics in the future, but this can only be classified as an educated guess at this stage. Ukrainian officials continue to urge citizens to remain vigilant and report any suspicious online activity.
This latest example of cyberwarfare underscores yet again the importance of robust digital defenses, from an individual scale up to country-level digital infrastructure. Regarding the prevailing situation, we believe Ukraine's ability to withstand these attacks will depend on its continued collaboration with international partners and its ongoing efforts to strengthen its cybersecurity infrastructure.


