A sophisticated phishing campaign using a phishing service called EvilProxy is targeting high-level executives in the US by exploiting a vulnerability in the popular job search website Indeed.com.
Indeed.com is a legitimate job search site which is used by millions of people from all over the world. Malicious actors have begun to take advantage of that trust. Let’s take a more detailed look at what’s happening.
Attackers Use Open Redirection on Indeed.com to Bypass Email Filters
The attack was first reported in a blog by the cybersecurity firm Menlo Security. The attackers are using a classic phishing technique called open redirection where they redirect people from Indeed.com to a Microsoft login page asking for their financial details. The login page is, of course, fake and has nothing to do with the actual Microsoft site.
By abusing the trust placed in Indeed.com by major email platforms, the phishing emails are able to bypass traditional email security filters.
Menlo Security first observed the campaign in July 2023. The phishing emails contain a link that appears to lead to Indeed.com but instead sends victims to the phishing site hosted on malicious servers which are monitored by the attackers.
The phishing page is built using the EvilProxy tool, which is designed to steal all the details from the Microsoft page by intercepting requests being exchanged between users and the site.
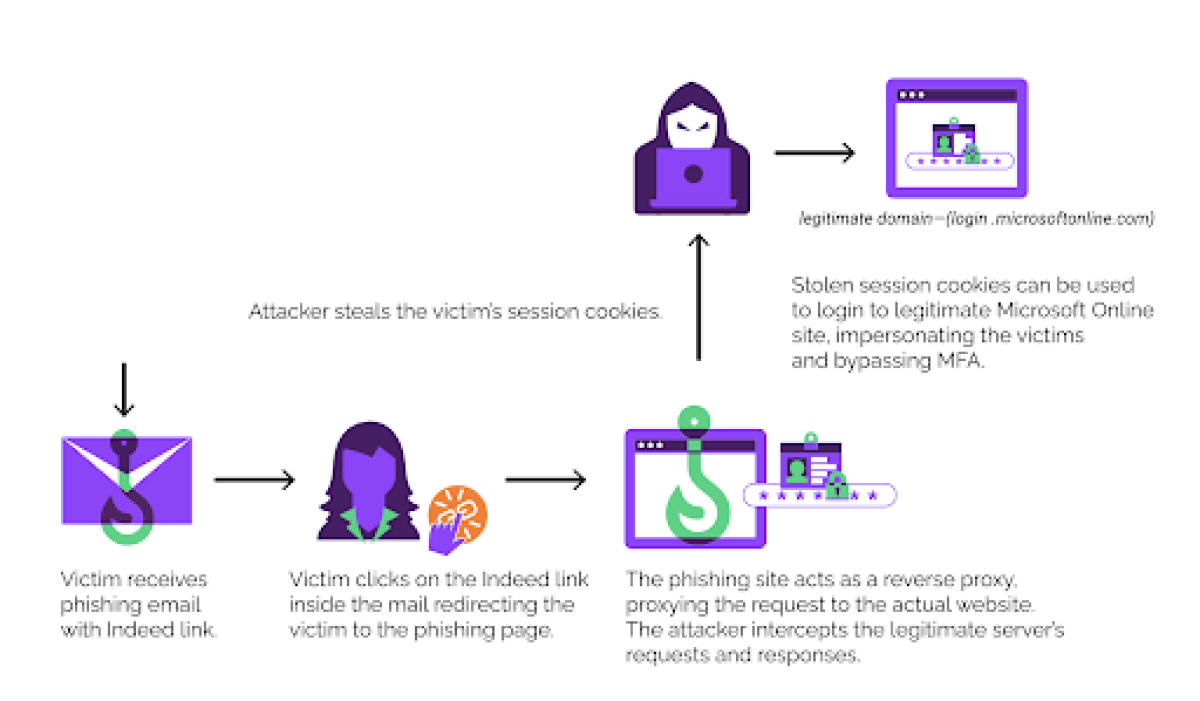
How the phishing attack happened. (Source: Menlo Security)
Executives at Major US Firms Targeted for Account Compromise
Before you begin to panic and think that you may have been a victim of this attack, keep in mind that most people who have been targeted are US-based executives who work in senior roles in industries such as banking and finance, insurance, real estate, and manufacturing.
The attackers seem to be focused on high-value individuals like C-suite executives who likely have access to sensitive company data.
By first compromising a senior executive's Microsoft account credentials, the attackers gain a foothold in the target organization. From there, they could potentially move laterally within the network to steal intellectual property, sensitive documents, or funds through business email compromise scams.
The phishing tool EvilProxy is also capable of stealing a user’s session cookies, allowing the attackers to bypass Microsoft’s multi-factor authentication and get access to the user’s account.
Indeed’s Popularity Has Exacerbated the Situation
Indeed's immense popularity as a job search website means phishing filters are less likely to block links to its domain. As mentioned above, this trust in Indeed.com is being exploited by these attackers to bypass traditional email security.
Menlo Security reached out to Indeed and reported the open redirection vulnerability, but it’s still unknown whether the job search site has done anything to fix the issue. Until they do something, the site will remain vulnerable to phishing attacks and we recommend avoiding it.
Initial Compromise Can Lead to Greater Damage
This campaign bears similarity to other recent phishing attacks that also redirected victims through trusted sites like YouTube before taking them to the phishing site. The use of legitimate sites helps add credibility to what are ultimately fraudulent links.
Stealing your personal and financial data is just the tip of the iceberg. Once the attackers have all your information, they can steal sensitive data, install ransomware and not release your data until you’ve paid them, or start an unauthorized wire transfer. All of these can easily lead to financial and, if you’re a big company, reputational damage.
The best way to deal with such attacks is for organizations to properly train their executives and employees who have access to confidential information. They need to know what phishing attacks look like and have the necessary tools, such as an antivirus like TotalAV, to combat them.


