Reports have emerged of a new hacking group on the dark web called Ransomed.vc, which claims to have breached all of Sony's systems in a ransomware attack. This is the first time since the PSN hack in 2011 that Sony has suffered a major breach.
Let’s take a look at what happened, who this new group of hackers is, and what is Sony’s response to the data breach.
First Reports of the Breach
The Australian cybersecurity publication Cyber Security Connect was the first to report the breach. According to an article posted on the site on 25th September, Sony was allegedly compromised by Ransomed.vc, a recently formed group of hackers that has only been active since September.
Cyber Security Connect has suggested that the group may have connections to previous dark web forums, so it may have been operating longer than we know.
What Data Has Been Breached?
The publication states that the purported hack revealed screenshots of Sony's internal login page, an internal PowerPoint presentation detailing test bench specifics, Java files, and a file tree containing 6,000 total files from the breach.
On the sites where they’ve leaked the data, the group said that they’ll be putting it up for sale and they won’t ransom it since Sony seems reluctant to pay for it.
"We have successfully [compromised] all of their systems," Ransomed.vc said, "We won't ransom them! We will sell the data, since Sony doesn't want to pay. The data is for sale now. We are selling it."
Reportedly among those 6,000 files is extensive documentation, including unknown "build log files," numerous Java resources, and HTML data. Much of the data is said to be in Japanese. While Ransomed.vc has not listed an asking price, the group provided their Telegram, Tox messaging service, and email for Sony to get in touch.
They’ve also stated that if no one purchases the data by September 28th, they’ll post all of it on the dark web.
So Who Is Ransomed.vc?
The group that’s behind the Sony breach has tried to legitimize themselves in order to extort their victims.
According to Cyber Security Connect, Ransomware.vc appears to operate as both a ransomware group and a ransomware-as-a-service organization. This means that in addition to large-scale corporate breaches like the alleged Sony hack, Ransomed.vc (which Cyber Security Connect claims is based out of Russia and Ukraine) also works with EU data protection laws to report security flaws and data privacy violations in company systems.
They take advantage of these data protection laws (such as GDPR) to pressure their victims into paying them.
The group doesn’t do the hacking themselves. Instead, they hire other hackers to do the dirty work for them. According to Flash Point, they recruited “affiliates” earlier this year and have now closed hiring since they feel they have hired enough people.
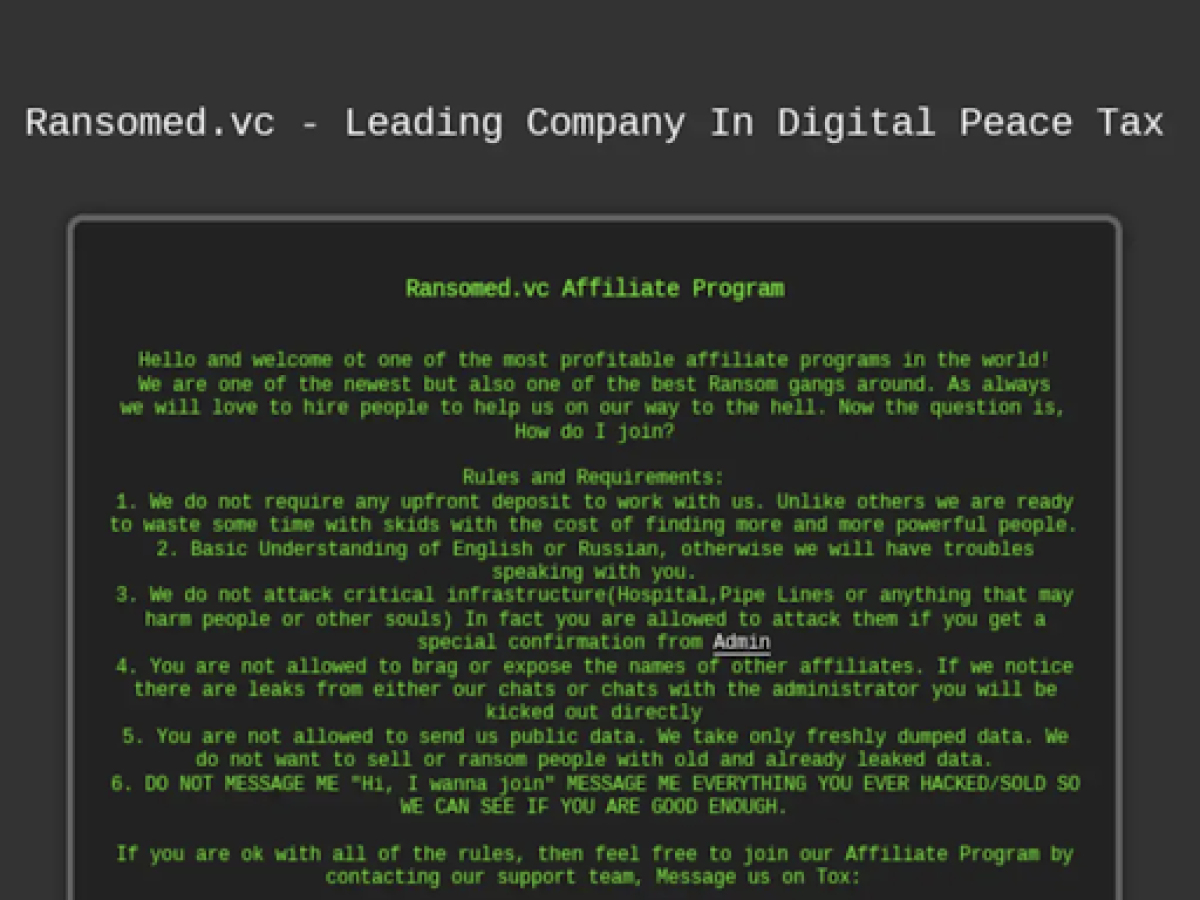
Ransomed.vc’s affiliate recruitment page. (Source: flashpoint.io)
What Is Sony’s Reponse?
Sony has said that they are investigating the claims and are looking into the situation, but they have refused to comment further. While 6,000 files may seem minor compared to the PSN hack that occurred in 2011, any security breach is serious, especially for a company as big as Sony.
Hopefully, Sony will be able to give a more detailed answer and work on making their systems safer and more secure.


