The LockBit ransomware group has been one of the most notorious on the dark web and has been particularly prolific in their nefarious operations. With this, the group came into the spotlight and, as a result, under fire from a number of different directions.
The latest news suggests that the group has been facing off against government agencies from the US, Europe, and more. In this article, we’re going to take you through all of the developments so far, how they happened, and what’s going to happen next.
The Takedown by the FBI, Europol, and Others
In February 2024, a coordinated effort by Europol, the FBI, and law enforcement agencies from eleven countries aimed to disrupt the operations of the LockBit ransomware group. This involved taking down various aspects of their infrastructure and providing support to victims.
Europol and the FBI led the initiative, collaborating with agencies from Australia, Canada, France, Germany, Netherlands, New Zealand, Norway, Sweden, Ukraine, and the United Kingdom. This collaboration served to obtain a wider reach and potential effectiveness against LockBit's global presence.
The operation focused on disabling key components of LockBit's infrastructure:
- Domain Seizures: Over 11,000 domains associated with LockBit were seized, essentially shutting down their online presence and communication channels.
- Server Disruptions: Authorities identified and disrupted 34 servers located in various countries, impacting their critical infrastructure for control, storage, and communication.
- Account Closures: Over 14,000 accounts linked to LockBit affiliates were identified and closed on platforms like Mega, Tutanota, and ProtonMail. These accounts likely served various purposes within the group's operations.
LockBit's Response
Following the takedown, LockBit claimed the FBI "hacked" them and threatened to release sensitive data stolen from Fulton County, Georgia, in January 2024. They claimed this data included information related to the ongoing criminal prosecution of former President Trump.
However, the FBI admitted to exploiting a known vulnerability in LockBit's infrastructure to gain access to their servers, not a traditional "hack." The irony of a ransomware group getting themselves hacked aside, this distinction is important, as it highlights the proactive efforts of law enforcement rather than a passive security breach in LockBit’s systems.
Deciphering the Technical Parts
While LockBit claims a "hack," the FBI explained that they simply exploited a known vulnerability in LockBit's PHP software. This doesn't involve actively breaching their systems in the traditional sense but rather taking advantage of existing weaknesses.
The takedown undoubtedly disrupted LockBit's operations, forcing them to rebuild their infrastructure and potentially hindering their ability to launch attacks. It hasn’t ended their operations entirely, however, as the group is already back on the dark web and has uploaded a note about the situation. A snippet of this note is shared as follows:
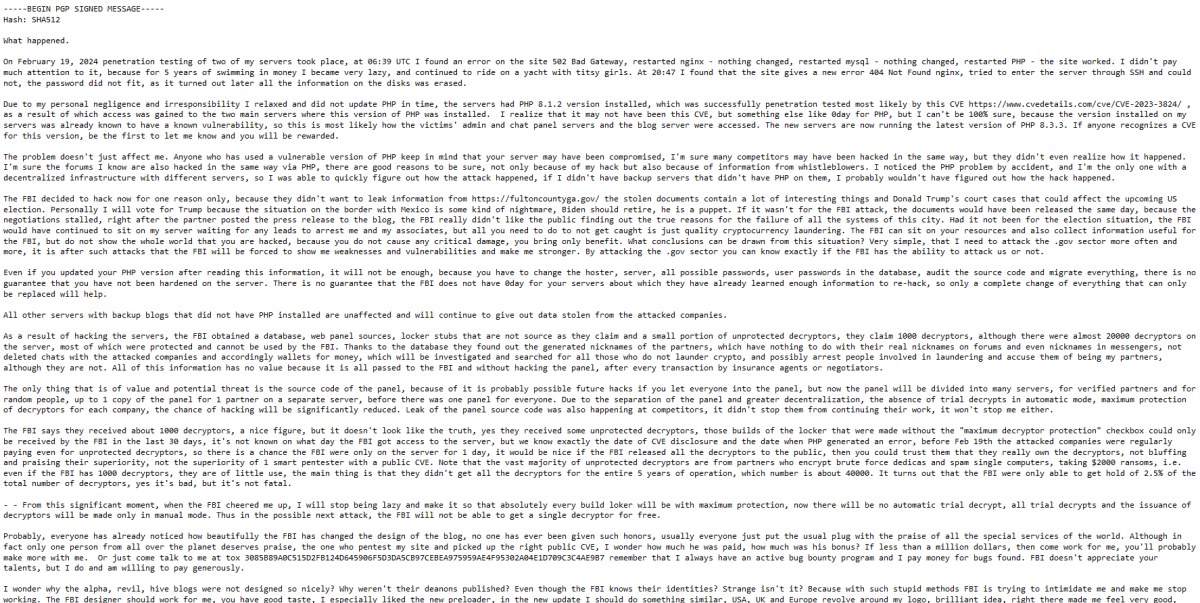
How the Situation is Developing
Experts remain skeptical about the true nature and importance of the stolen data. Some speculate it might be less sensitive than LockBit claims, aiming to create unnecessary fear for ransom leverage.
In response, somewhat complacently, Fulton County officials have downplayed the significance of the data leak, emphasizing strong security measures in place and stating "no mission-critical systems" were compromised. As of February 29, 2024, LockBit is still threatening to release the stolen data unless a ransom is paid. Only time will tell how this scenario ultimately plays out.


